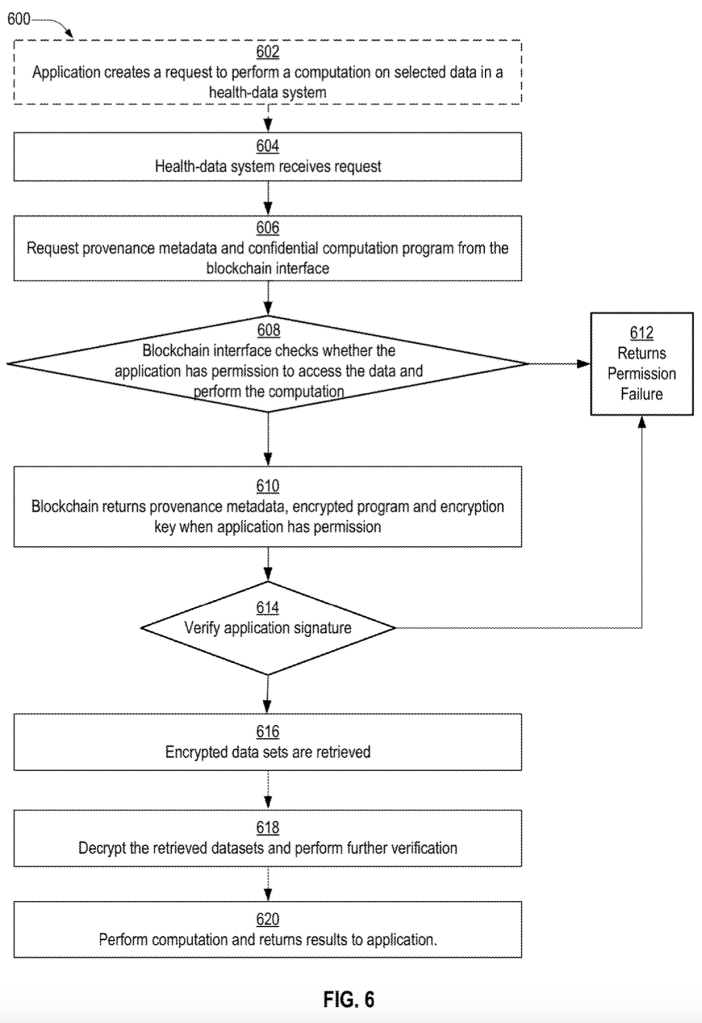
The THaW team is proud to announce the issuing of a patent for a secure, integrated data system and method that employs blockchain and Trusted Execution Environment (TEE) technologies. This method achieves information provenance for data, particularly, mobile health device data.
Using a blockchain to record and enforce data access policies removes the need to trust a single entity with gatekeeping the health data. Instead, participants form a consortium and collectively partake in verifying and enforcing access policies for data stored in private data silos. Data access and computation takes place inside of TEEs, which preserves data confidentiality and provides a verifiable attestation that can be stored on the blockchain for the purpose of information provenance.
This ensures that patients have confidence in the privacy of their original health data that may be managed by multiple entities, and provides security and information provenance for that data while it is aggregated or transformed during interactions between patient and healthcare professionals.
To learn more, check out the patent! Organizations interested in this patented work are encouraged to contact the authors.
Hardin, Taylor, and David Kotz. Data system with information provenance. US20210273812A1, issued September 2, 2021. https://patents.google.com/patent/US20210273812A1/en.